#Interview
Here, it is a corner to interview various people, receive new opinions and think more about security.
#Interview for Associate Professor Kazunari Omote /University of Tukuba

This time, we have covered the associate professor at Tsukuba University who is familiar with information security.So I got a variety of professors about security so I would like to share it here with diagrams.
*As for the Interview page, since there was some correction, we corrected and deleted some of the questions under the guidance of the faculty professor.
Q1:How can I improve password security more?
A1:First, I will explain from the threat.If the password is leaked it leads to the attacker going to it.Also, a lot of leaked passwords are gathered by researchers, which are applied to AI and the characteristics of passwords are analyzed.For example, capital letters capital letters come first at the beginning, numbers end at etc.
Ideally, it is better to use a password generation tool.(Characteristic does not appear due to high randomness)However, from the viewpoint of convenience, the disadvantage of being hard to remember comes out.
Also, password usage is bad.Because it leaks out one place and it gets out all.However, there are opinions that it is better to stop changing passwords on a regular basis.
Because it is easy to distinguish between similar things and easy to remember features, making analysis easier.
To keep the password safe, it is important to use passwords according to importance of service.
Also, security that protects important information is said to be more severe with one step of authentication.From now on, it seems that it will shift to other factor authentication and two-step verification.(For example,Online banking)(Figure↓)
Security is directly linked to the cost of service installation and operation.Some cost very expensive.So, keeping the place to protect depends on the basic idea of security. There is no need to lay out security where there is no need.Not all security is high in everything.
For example, banks and others are required to have high security, but personal computers do not require such high security.
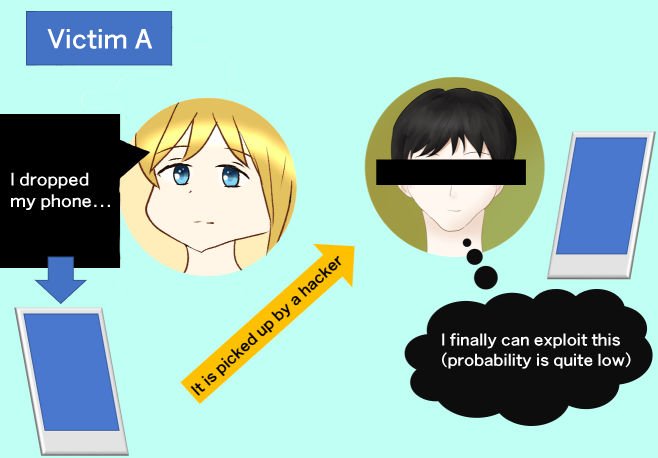
Why did the password change from 8 digits alphanumeric to 4 digit PIN on Windows 10?(Face authentication is also the same and accuracy is not very good) This is because the probability that a person picking up the terminal is a hacker is extremely low when we suppose that nobody other than you can log in unless you drop the terminal, we put emphasis on convenience. (Figure↓)
Q2:What kind of things will come out of Biometrics in the future?
A2:It is expected to enter ... .... Biometrics will be selected by cost and convenience.
First, from fingerprint authentication. Fingerprint authentication is cheap but easily broken.For example, fingerprints can be copied from a fingerprint attached to a glass, fingerprints are analyzed from photographs, and so on. Vein certification is said to replace it. The vein is inside the body, so it can not be copied.However, there is a disadvantage that the cost will be considerable at this stage. However, it is thought that cost can be suppressed to some extent if it is popularized.
Next is iris authentication. This will cost you, but both convenience and security are excellent.Also, since face recognition technology has many misidentifications, it can not be used in important places. Besides, there is DNA authentication.Currently, it is the most accurate authentication method. However, there is a possibility of misunderstanding in relatives because the parent and child's DNA are close.
Vein and iris authentication technology which is excellent in convenience, accuracy and security are expected to become mainstream now.
Q3:Security software that occasionally falsely detect Security software Is it actually necessary?
A3:The meaning to put in is that it will detect suspicious programs with high priority.
Let's start from the case of individuals. In the case of individuals, it is possible to put in your own terminal unless so important data is included. However, there is a possibility that an attack that takes yourself as a stepping stone will be done.(When you become an assailant while you do not know.(Figure1))。
Security software will not detect all attacks, but it will detect important attacks and it is important to keep it installed. Furthermore, by taking such minimum measures, we can assert measures and also have the advantage that we can protect ourselves from the mass media and others.
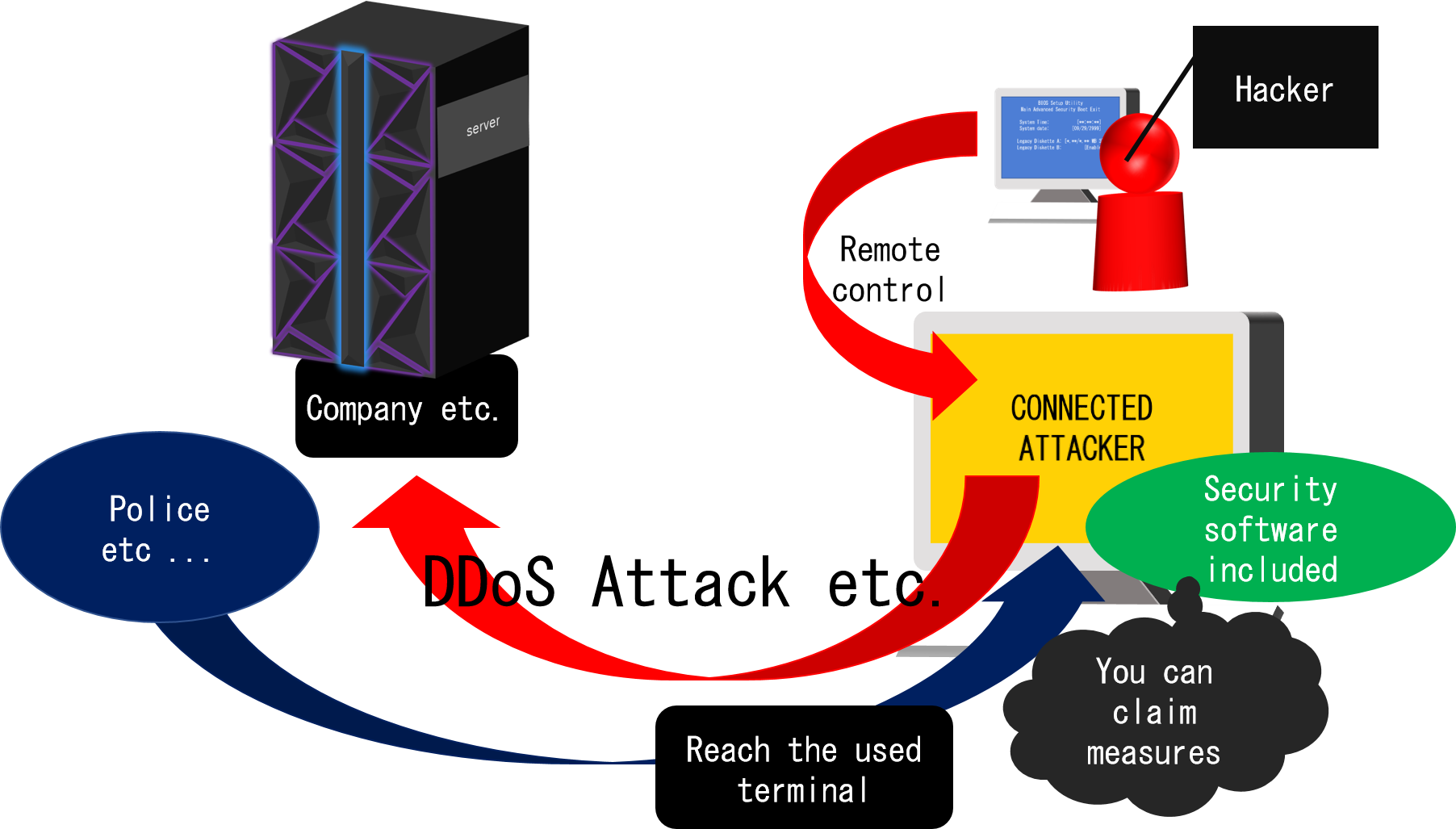
(Figure1)
In the case of an organization, in most cases, it is obliged to be included in the policy of a company in most cases. Like an individual, it detects important attacks. However, in case there were information leaks and so on, it is possible to make a claim to protect the enterprise as having done the least. In other words, it helps not only to protect information, but also to protect the face.

Q4:I heard that there are lots of Vulnerability in IoT, but how much is actually there? Also, how can we take measures?
A4:The primary reason for IoT's Vulnerability is a weak password.There are many things with no password and weak passwords.t is illegal to break the password being honored from the perspective of the law, but seeing things without a password is gray zone because it is considered to be open. It can be said that security literacy is multiplied. For example, it is a security camera.(There is actually a site where you can see security cameras all over the world) It is important to know that there is a need to revise the perception of those who think they are just connecting.
Since the number of units is fundamentally large, the place where security patches are adapted properly comes to importance.The minor equipment may be delayed in response.
Q5:How do you find Vulnerability?
A5:There are two patterns in roughly divided.One is a method that will be found in the survey from inside. The other way is to be discovered from the outside.(This includes happening by good people to happen, and finding for malicious purposes by malicious persons.) Basically, if you are open source, there are ways to discover the portion considered to be Vulnerability from code by experience, and to do Experiment.(Good corporations, including malicious hackers as well)When an ordinary person finds it, it is reported as a defect. Since it may lead to Vulnerability as well, if you find it, let's report it to the manufacturer.
Q6:Please tell me about the threat to security caused by the appearance of quantum computers.
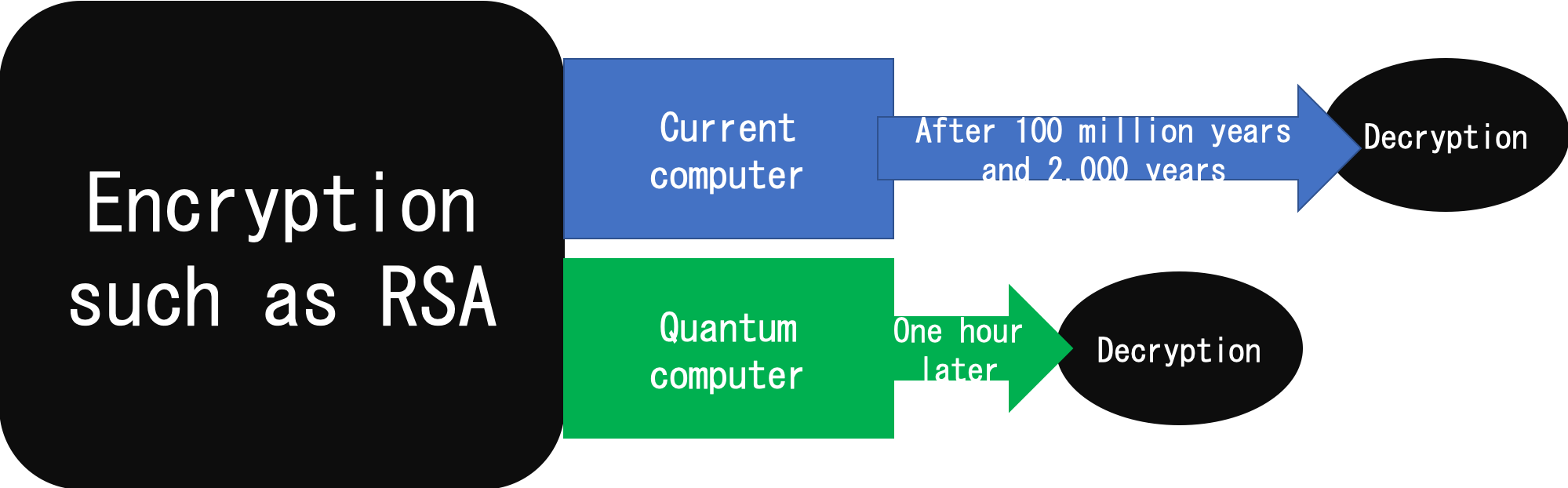
A6:I think that it will be a while ago a little.The cryptographic research is just beginning.(Called quantum cryptography)As quantum computers come out, traditional encryption such as RSA and elliptic curves will be broken, so we need new cryptography research in preparation for that. It is not practical level yet.For example, it takes 1 billion years to decrypt on current computers, even encryption methods can be solved in one hour with quantum computers.So, we have to develop an encryption method that takes a billion years even with a quantum computer. Simply, it becomes necessary to change the problem rather than extending the digits.
Q7:We often hear loss news on Virtual Currency, is that a company's fault?Or is there a Vulnerability in the block chain?
A7:The block chain was never broken until May of this year (2018), which was caused by negligence on the exchange side.However, in May of this year, the block chain of the currency with the low computing capacity of mining is broken, and the risk that the service with few participants in the block chain is aimed at is increasing.
Q8:What will be the usage of block chains in the future?
A8:Now I can not say it, I feel like fumbling. Even our research group is just exploring while doing research.
Q9:What is the security of the P2P method?
A9:P2P is basically a network that anyone can join.Everyone can join the P2P block chain network.To increase the security of P2P like this KYC(Known Your Customer)is important. It can be said that it is quite a hurdle to realize this with world standards.
Finally, Article 9 of the Basic Law of Cyber Security states that "People shall strive to deepen their interest and understanding of the importance of cyber security, pay attention to securing cyber security, based on the basic philosophy." In other words, it states that it is necessary for the people to strive to counter cyber security. I hope this web page will be of help.




