
#About this page
Here will explain "Security Of IoT"
 IoT has become famous
IoT has become famous
 New things and risks adjoin each other.
New things and risks adjoin each other.
 Specific damage etc.
Specific damage etc.
 Solution for now
Solution for now
 Summary
Summary
Here will explain "Security Of IoT"
#IoT has become famous
IoT is an abbreviation of internet of things, as it was in chatting, everything in the house is connected to the Internet and can be controlled. In other words, saying "turn on the light" to Google assistant or Siri means that house electricity is turned on, and saying "cooler on" will put on a cooler.
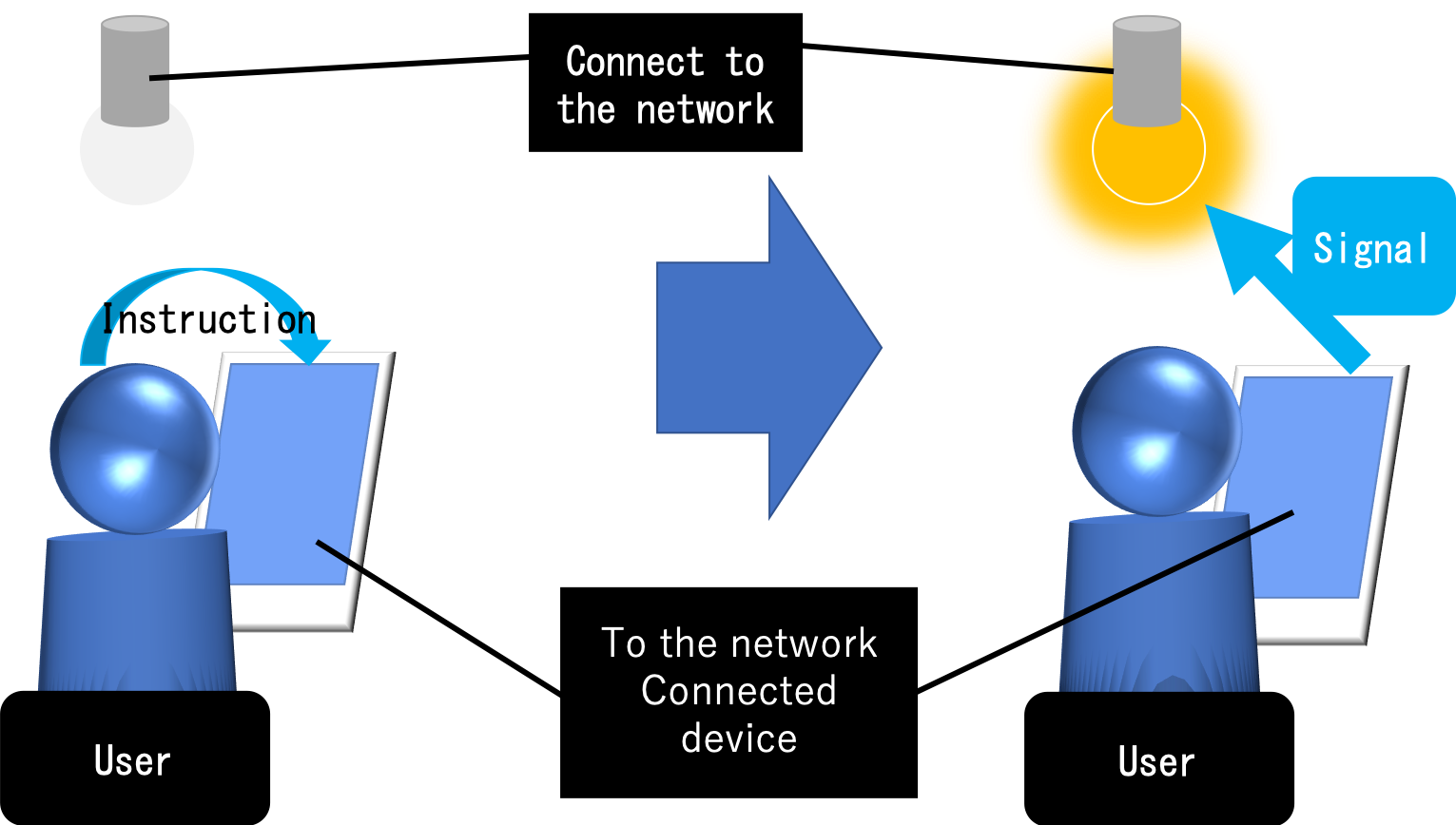
#New things and risks adjoin each other.
Such a system is a new technology being gradually introduced to home. However, this system is new, there is a possibility that vulnerability (weak point) is still going down still. Of course, each company has a program so that there is no vulnerability. However, it is what human beings are making, so the defect will inevitably come out.
As soon as Vulnerability is discovered, security patches (weakness improvement updates) will be produced. However, production takes a long time. It will take nearly a month at least, at least. You must be careful not to run out of control of what you possess, under control of yourself. In order to do that, you must know exactly what risks you have and you need to know the remedial measures. Let's take a closer look.
#Specific damage etc.
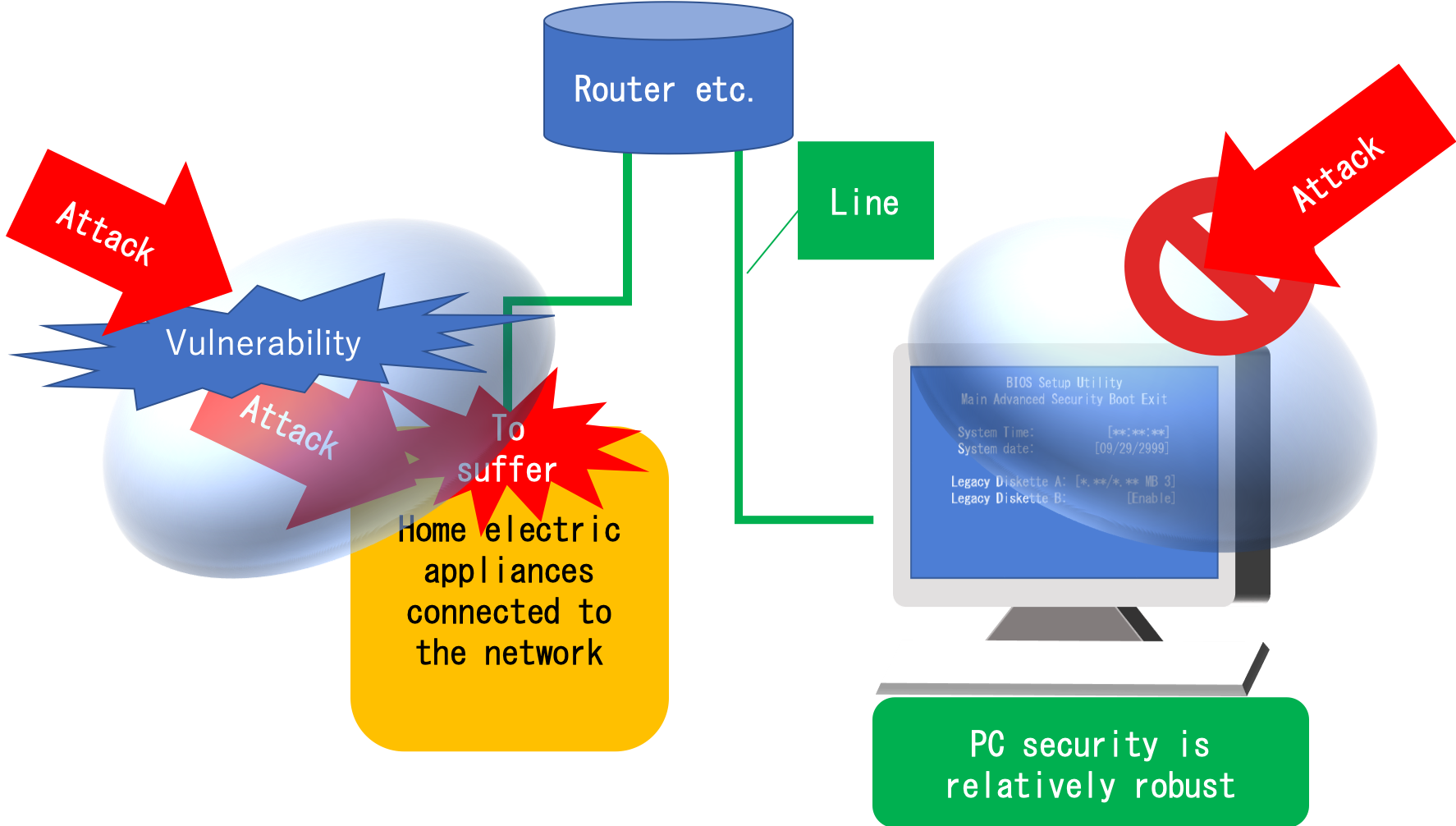
Hacking with Vulnerability is a risk that can be caused by IoT. Hacking means that a terminal under your control is hijacked by a third party and becomes uncontrollable, or your terminal is misused. What will happen if your terminal (eg smartphone) becomes uncontrollable? Is not there some people who can not work? In this way you may have a big loss to yourself. Also, if your terminal is misused it will be more difficult.
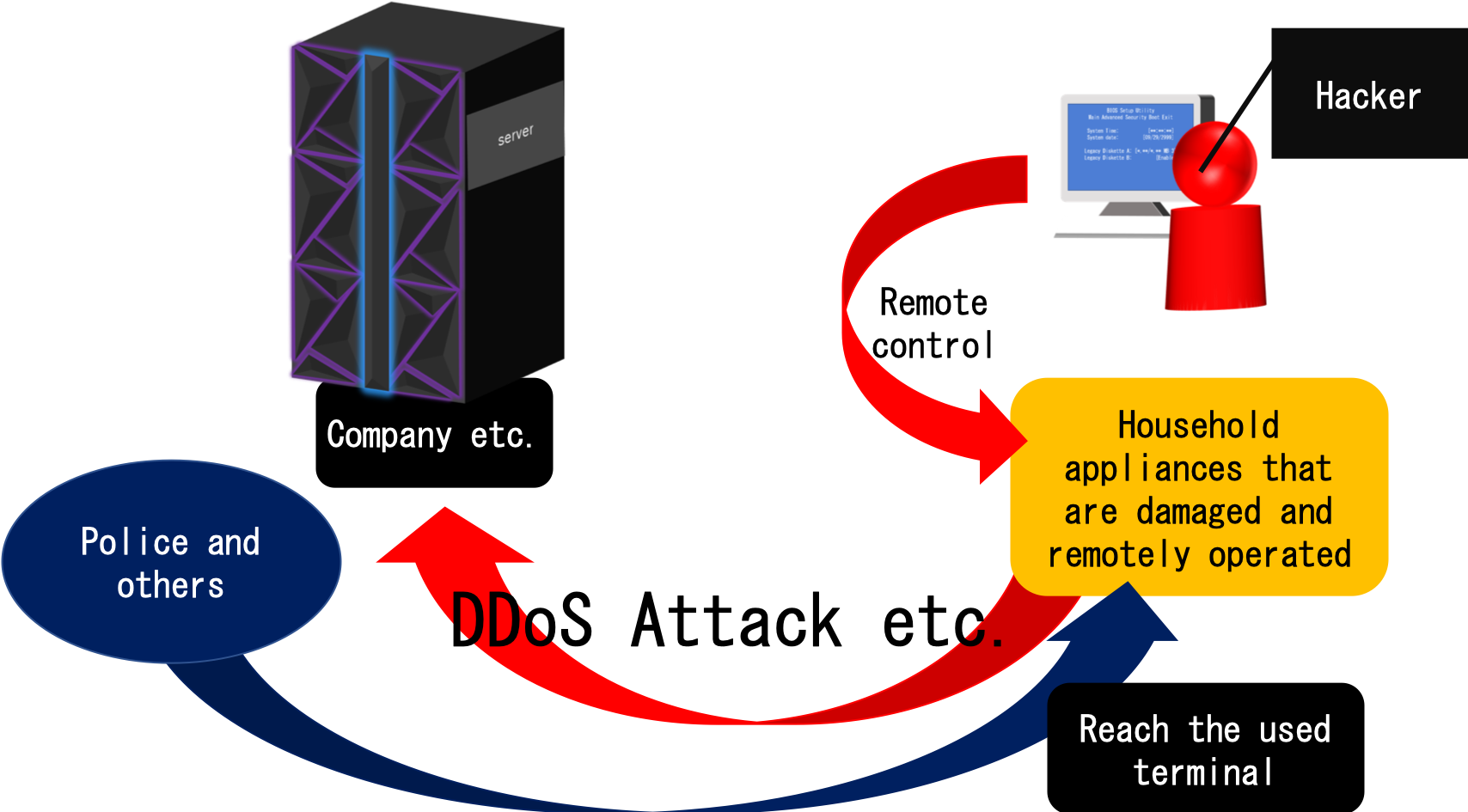
If your IoT device is used for crime such as server attacks against companies or DDoS attacks, the police side analyzes the information of the terminal and searches it, so there is the possibility of making a false charge. Moreover, it will be quite difficult to prove innocence. Without knowledge it is near impossible. In this way it may be sometimes tailored to perpetrators.
#Solution for now
In order to avoid such things, it is necessary to ensure the security of the core terminals (mainly smartphones). (For details, go to the security page) In addition to introducing security software to prevent intrusion into the smartphone, periodic virus scanning, if there is a household appliance that is acting strangely, immediately have expertise Contacting a supplier is also a hand.
In the future information society, knowledge will become indispensable. Also referring to IT news etc. if Vulnerability is discovered in the terminal that you own, you need to update the software immediately following the company's instructions. People who are using old OS (service terminated) or who are not updating may be in danger because security patch has not been applied. Please update immediately.
#Summary
 Since it is a new system, it seems that there are many damages that used vulnerability. Let's update the latest version of security patch as soon as possible.
Since it is a new system, it seems that there are many damages that used vulnerability. Let's update the latest version of security patch as soon as possible.
 If there is a household appliance that is acting strangely, immediately contact the trader.
If there is a household appliance that is acting strangely, immediately contact the trader.